IT Policy – Approach
An important guideline in accomplishing goals is that of having an approach. Here is an approach that I believe will assist in reaching organizational goals.
An Industry Security Policy. One approach is basing IT Policy on exiting Industry (industry as in the industry an organization operates in) security policy and applying it to IT where there is intersection. One example of an industry policy is that of HIPPA as it relates to the health care industry.
HHS.gov gives us the background of HIPPA as follows:
“The Health Insurance Portability and Accountability Act of 1996 (HIPAA) required the Secretary of the U.S. Department of Health and Human Services (HHS) to develop regulations protecting the privacy and security of certain health information.1 To fulfill this requirement, HHS published what are commonly known as the HIPAA Privacy Rule and the HIPAA Security Rule. The Privacy Rule, or Standards for Privacy of Individually Identifiable Health Information, establishes national standards for the protection of certain health information. The Security Standards for the Protection of Electronic Protected Health Information (the Security Rule) establish a national set of security standards for protecting certain health information that is held or transferred in electronic form. The Security Rule operationalizes the protections contained in the Privacy Rule by addressing the technical and non-technical safeguards that organizations called “covered entities” must put in place to secure individuals’ “electronic protected health information” (e-PHI). Within HHS, the Office for Civil Rights (OCR) has responsibility for enforcing the Privacy and Security Rules with voluntary compliance activities and civil money penalties.” [1]
As a healthcare organization for example, the HIPPA can serve as the backbone/foundation of IT Policy (that can be built upon) being that in order for the organization to be in business it must be HIPPA compliant. For all day to day operations or strategic projects, the organization can assess any incoming changes or actions by referring to their HIPPA inspired IT policy to ensure that they are being compliant to their IT policy which indirectly keeps them compliant to HIPPA. In taking this approach it makes it harder (or at least riskier, thus justifying “enforcement”) for organizations to stray away from IT policy as not following policy risks the entire organization not being compliant to the overall policy of their industry thus creating a greater sense of importance organization wide. These ultimately fulfils business requirements as the creation of the IT policy meets the needs of the business, and the actual policy fulfils the functional requirements.
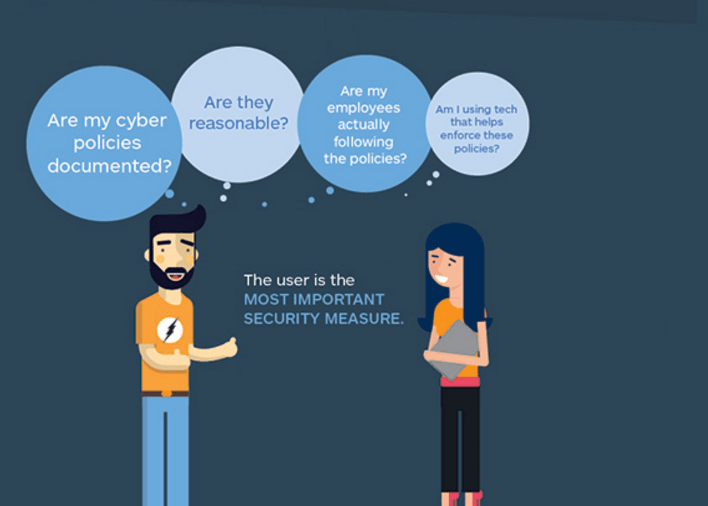
Image Courtesy of Malwarebytes Lab
References:
- 2013. Summary of the HIPAA Security Rule. (July 2013). Retrieved February 17, 2018 from https://www.hhs.gov/hipaa/for-professionals/security/laws-regulations/index.html
Acknowledgement:
IT7833 Exercise 4 – Creating Value